Design of security policy management for software products
October 30, 2023
Table of contents
Quick Access
The need of good security rules for software products cannot be overstated in an increasingly linked world. Organizations and software developers must invest in the design and execution of robust security policy management systems as the digital ecosystem evolves.
This article examines the basic ideas and concerns for establishing security policy management for software products, emphasizing the critical role it plays in safeguarding sensitive data and retaining user confidence.
What is a security policy?
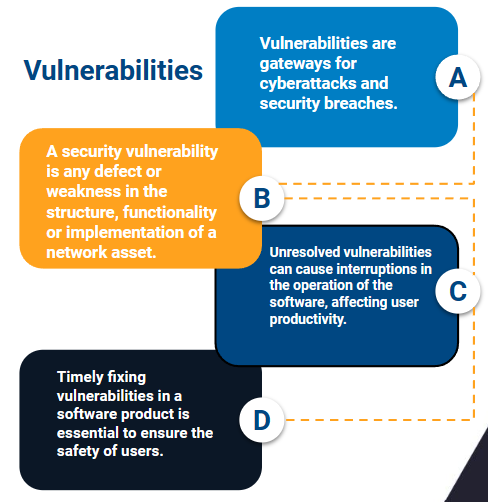
When working on a software product, a security policy is any regulation or statute that is applied so that the data and everything contained in this product is not vulnerable to cyber attacks or any similar situation.
An example of a security policy could be the HIPAA statute, applied to software projects for healthcare institutions. HIPAA stands for the Health Insurance Portability and Accountability Act, which is a United States federal law that was enacted in 1996. HIPAA has several provisions, but one of its primary purposes is to protect the privacy and security of people's health information.

The importance of security policy management
Security policy management involves defining, implementing and monitoring the rules and procedures that govern an organization's approach to protecting its software products. These policies are essential to maintain the integrity, confidentiality and availability of data and services. They act as a proactive defense mechanism against possible threats and vulnerabilities.
Steps to design a good security policy
1. Define clear objectives
The first step in designing a security policy management system is to define clear objectives. This involves understanding the specific security needs and objectives of the organization. Consider the following questions:
- What are the critical assets and data that need protection?
- What are the regulatory compliance requirements for the software product?
- What are the risks and potential threats relevant to the product?
- By addressing these questions, you can establish a framework for designing security policies that align with your organization's unique needs.
2. Risk assessment
Conducting a comprehensive risk assessment is crucial to identifying potential vulnerabilities and threats. A risk assessment helps prioritize security measures and allocate resources efficiently. It involves assessing the likelihood and impact of various risks and determining which security policies and controls are most critical to mitigating these risks.
3. Policy design
Designing security policies involves defining a set of rules, standards, and procedures that describe how to protect the software product. These policies can cover areas such as access control, data encryption, network security, incident response, and more. When designing policies, consider the following:
- Accessibility: Policies should be easily accessible to all relevant stakeholders, including developers, IT administrators, and end users.
- Clarity: Policies should be written in clear, understandable language, ensuring that everyone can understand and comply with them.
- Customization: Allow flexibility in customizing policies to fit specific business and software requirements.
4. Implementation and compliance
Once security policies are designed, they need to be implemented and enforced consistently. This involves integrating security controls into the software development lifecycle, implementing security measures, and monitoring policy compliance. Automation plays an important role in ensuring consistent policy enforcement.
5. Training and Awareness
Educating and raising awareness among employees and stakeholders is essential. Security policy management should include training programs and initiatives to ensure that people are aware of and aware of current security policies. Training and regular updates are crucial as security threats evolve.
6. Continuous monitoring and evaluation
Security policy management is not a one-time effort; requires continuous monitoring and evaluation. Periodically evaluate the effectiveness of security policies, track security incidents, and adjust policies as necessary. Continuous improvement is vital to stay ahead of emerging threats.
7. Incident response
Having a well-defined incident response plan is an integral part of security policy management. This plan describes how to respond to security incidents, mitigate their impact, and recover from them. Clear communication and quick action are essential in the event of a security breach.

Final thoughts
Designing security policy management for software products is a critical aspect of cybersecurity. It ensures that organizations can protect their valuable assets and data while maintaining the trust of their users.
By defining clear objectives, conducting risk assessments, designing effective policies, implementing and enforcing them, and continually monitoring and adapting to changing threats, organizations can build a resilient security framework that keeps their software products secure in an evolving digital landscape. constant evolution.
Remember that cybersecurity is an ongoing effort and adapting to emerging threats is key to long-term success in protecting software products.
We recommend you on video
Related Blogs


How to integrate UiPath RPA with a database

Magento Development Services for the Healthcare Industry
Best Practices for Hiring a Drupal Developer

5 steps of UiPath RPA implementation


